The digitalisation of products and processes brings not only opportunities for banks and payment service providers, but also an increasing number of risks. Cyber attacks and IT failures can cause enormous financial and reputational damage. This is where DORA, the Digital Operational Resilience Act, takes action. This EU regulation aims to ensure that financial institutions become more resilient against threats targeting their technical infrastructures and that cyber security is prioritised across the entire organisation.
In this article, we take a closer look at the requirements DORA places for banks and payment service providers and how companies can take action to fulfil these.
Was ist DORA?
The Digital Operational Resilience Act (DORA) is a key EU regulation that aims to strengthen the digital operational resilience of the financial sector. It intends to ensure that banks and payment service providers are robustly prepared against cyber attacks, IT failures and other digital threats. The regulation sets out general standards for IT security, particularly in the areas of information and communication technology (ICT) risk management, the reporting of ICT incidents and the monitoring of risks by third-party ICT service providers.
Highly efficient and stable ICT structures shall create more security in the financial system and minimise the risks of digital transformation for market participants. This will lead to a significant growth in the analysis and reporting requirements for financial institutions. DORA will place the current high outsourcing rate of banking IT and banks’ strategies for digital transformation in the focus of supervisory authorities.
DORA already came into force on 17 January 2023 and will fully apply from 17 January 2025 on. Financial institutions must therefore achieve DORA compliance until January 2025.
The schedule of DORA (2023-2025)
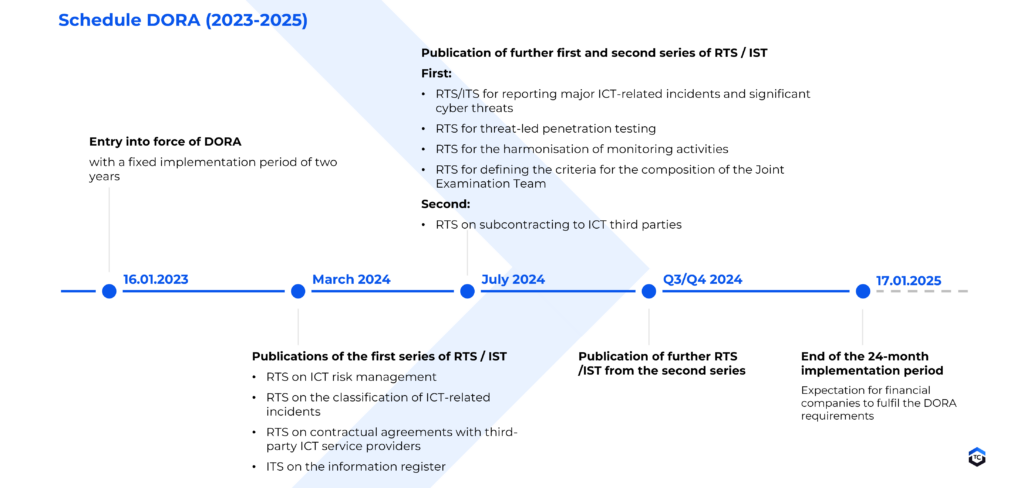
On July 8, 2024 the BaFin (Bundesanstalt für Finanzdienstleistungsaufsicht) published a supervisory statement regarding DORA. It contains extensive implementation guidelines for ICT risk management and ICT third party risk management, among other topics. The guidelines are not mandatory but provide assistance and explanations for organisations to fulfil the DORA requirements. Beyond that the supervisory statement compares the existing IT requirements (BAIT/VAIT) with the new DORA requirements. In providing the supervisory statement, BaFin states that existing IT requirements (BAIT/VAIT) are largely covered and expanded by DORA. With the national implementation of the FinmadiG (Finanzmarktdigitalisierungsgesetz), BaFin plans to suspend previous IT requirements (BAIT/VAIT/KAIT/ZAIT). Companies that are not covered by DORA still have to take proper action to deal with IT and cyber risks.
What are the main objectives of DORA?
Improving ICT risk management processes and ICT governance
DORA requires financial institutions to develop and implement ICT risk management systems. This includes the identification, assessment and reduction of ICT risks. Through standardised processes and regular reviews, risks should be identified at an early stage to take action immediately. BaFin’s implementation guidelines for DORA emphasise that the responsibility for ICT risk management lies within the management body of financial organisations.
Increasing resilience against cyber threats
Another goal is to strengthen actions to detect, prevent and respond against cyber threats. Banks and payment service providers need to develop plans for dealing with cyber threats and test these regularly. In addition to the retrospective view of ICT-related incidents and the performance of the ICT risk management scope in the past, new technological developments, including cyberattacks, should also be monitored. Financial institutions should be able to create a fast and effective reaction capability that enables the organisation to maintain business operations continuously.
Ensuring the continuity of critical functions
DORA requires the development of emergency plans and business continuity strategies. Financial institutions must ensure that critical functions can continue in the event of serious ICT incidents. Testing ICT security measures on a regular basis is key.
Strengthening monitoring and reporting of ICT incidents
DORA requires the reporting of serious ICT incidents to supervisory authorities and to analyse their sources. The aim is to create transparency for supervisory authorities so that effective control mechanisms can be implemented. By establishing an ICT asset management and categorising related risks, dependencies on third-party ICT service providers, risks from cyber threats and ICT vulnerabilities should be identified and regularly reviewed.
Supporting due diligence requirements for third-party providers
DORA sets a high value on due diligence in the selection and monitoring of third party providers of critical ICT services. Banks and payment service providers need to take appropriate security actions and ensure that their service providers are regularly reviewed. The DORA implementation guidelines set out enhanced contractual requirements for the use of ICT services, including minimum requirements for all contractual agreements and obligations to review and test. This minimises outsourcing risks and increases security along the entire supply chain.
Management of third party ICT risks
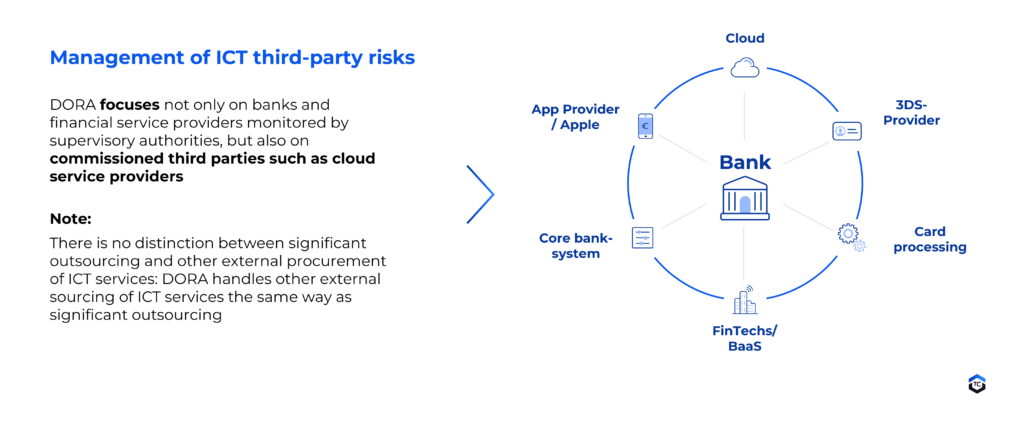
What specific action does DORA require from banks and payment service providers?
The new requirements are forcing banks and payment service providers to rethink and adjust their ICT risk management processes. The following actions should be taken to ensure regulatory compliance:
ICT governance and risk management: adaptation of internal guidelines and processes
Internal guidelines must be reviewed or established to reflect DORA’s new ICT compliance requirements and to ensure continuous risk assessment and management (including documentation of processes for providing documentary evidence to supervisory authorities). Moreover, an ICT risk control function must be established that is responsible for the management and monitoring of ICT risks.
Testing digital operational resilience: implementation of baseline tests and TLPT
Internal guidelines and operational processes must include regular, at least annual baseline testing and TLPT (Threat-led Penetration Tests) to identify and eliminate potential weaknesses. Cooperating with testing service providers can be considered in this context. Beyond that, it is necessary to consider extended scenarios such as climate change, insider attacks and large-scale power outages.
Disruption incidents and reporting obligations: establishing a reporting system
It is necessary to develop an internal reporting system for ICT incidents with defined processes and criteria for classifying and reporting security incidents. Financial companies must ensure that logs are protected against manipulation and loss and that all ICT systems are synchronised with a reliable time reference.
Management of third-party risk: ICT outsourcing management and monitoring critical ICT service providers
Reviewing and updating outsourcing guidelines, contracts and internal processes for analysing the risks of third-party providers, including regular due diligence methods, maintaining an information register and adapting tendering processes based on extended evaluation criteria. This includes minimum requirements for all contractual agreements as well as review, testing and cancellation rights.
In the course of 2024, there will be more specific legal acts in the form of technical standards (RTS and ITS) for most of the regulatory areas.
The impact of DORA at a glance

DORA is a challenging task for financial institutions, but it is also an opportunity to strengthen ICT security and resilience. Although the implementation of DORA requires significant effort and investment, it contributes to the long-term stability and security of the European financial sector.
How do we successfully support banks and payment service providers?
With our extensive consulting experience in the payment and banking sector, we are looking forward to supporting you in implementing the DORA requirements. In addition to dealing with the requirements of DORA in your company, we can contribute our knowledge and experience from various sourcing strategy and implementation projects. The requirements for outsourcing ICT services to third parties in particular are increasing significantly. New requirements include conducting risk assessment before a contractual agreement is concluded with a third party. In contrast to the MaRisk the DORA regulation no longer differentiates between outsourcing and other external procurement of ICT services.
Which means other external procurement of ICT services will also be covered by DORA in future, with corresponding due diligence obligations for banks or financial service providers. Sourcing strategies and existing outsourcing of ICT services should therefore be reviewed in order to take the requirements of DORA into consideration at an early stage and, if necessary, implement adjustments, for example in service provider management.
Are you looking for a way to develop secure and innovative processes, strengthen your digital resilience and get your company ready for the future? Please feel free to contact us.
What impact does DORA regulation have on your company?
DORA is part of our new workshop “NextGen Payments: Revolution or evolution by 2030?” In a customised workshop, we discuss with you how the future drivers of digitalisation, regulation and cyber security will affect your business models and we will work together to develop individual solutions. You can find more information here.
Further regulatory requirements – PSD3 und PSR
Alongside DORA, other regulatory requirements such as PSD3 and PSR are influencing payment transactions. Learn more in this blog article.

Jens Hegeler

Hauke Peters

